DegerPhish - Phishing-Awareness as a Service
With our phishing awareness tool
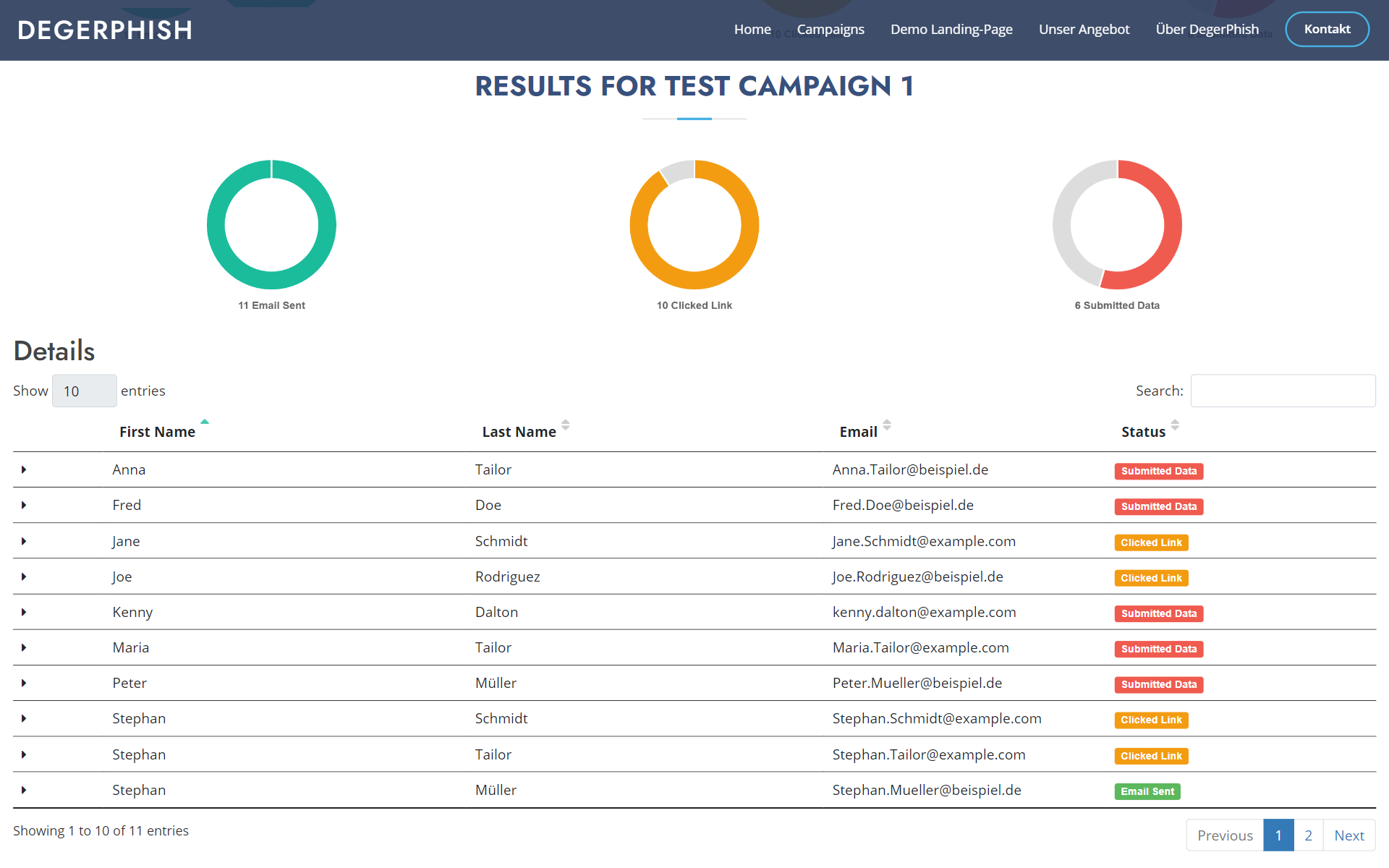
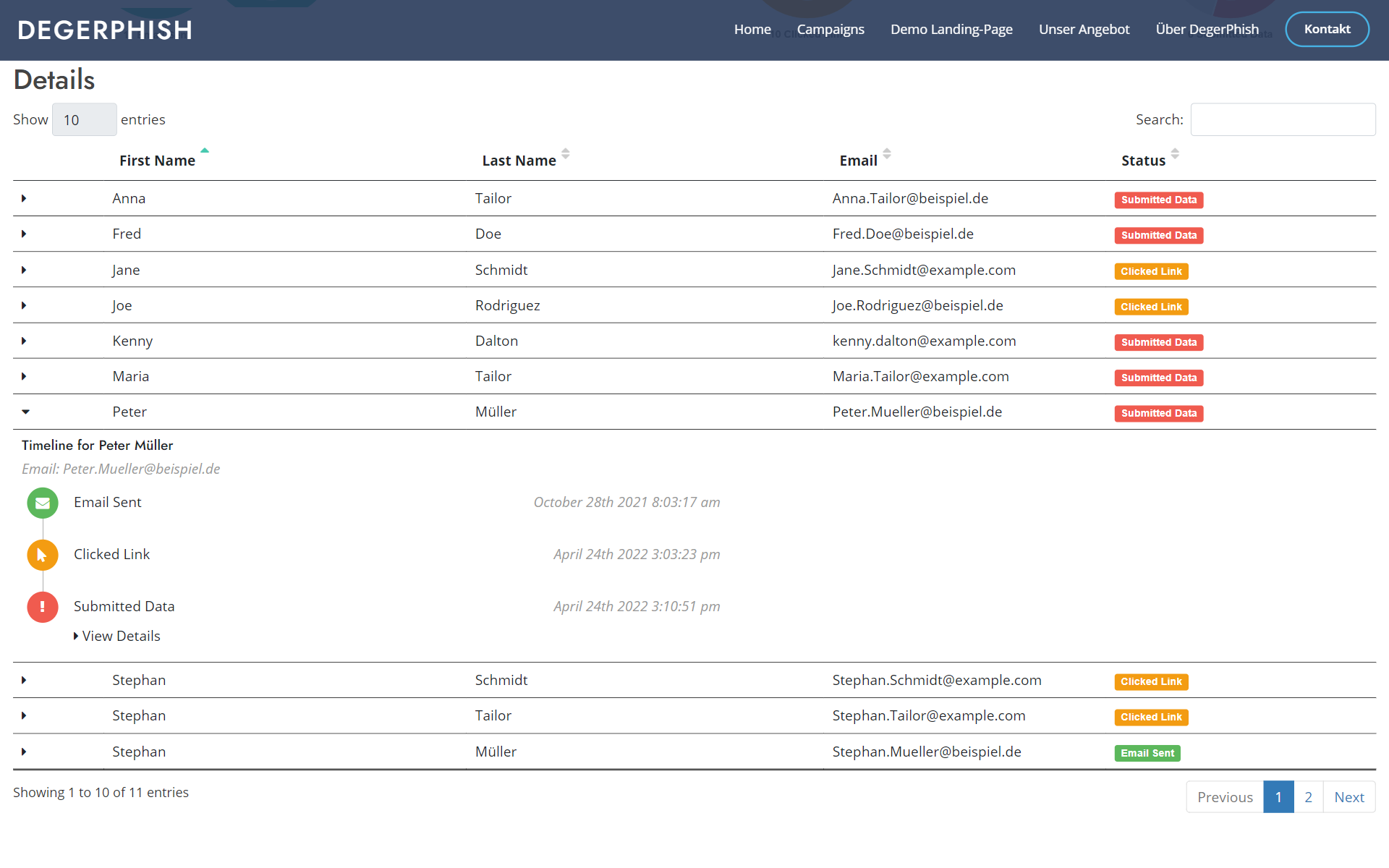
DegerPhish, you can send simulated phishing e-mails to your employees for awareness purposes and evaluate the reactions to the e-mails.
Features include:
- Can be used independently of other software systems
- Easy to use - no special IT know-how required
- Custom landing pages (i.e. the page users land on when they click links in the email)
- Reporting on user reactions
- Prompt users to enter data and evaluate that data
- Individual levels of anonymization / pseudonymization
- Server location in the EU/Germany
Of course, we only allow the use of DegerPhish for awareness purposes within the requestion company and not for illegal phishing attacks.
Cyber Crime

Each year cyber crime and hacker attacks on enterprises cause billions of euros in damage. Companies from a wide range of industries and sizes are affected. The damage can take different forms, e.g.:
- the manipulation of company websites
- the manipulation and sabotage of internal and external IT systems
- theft of customer, personnel or development data
- long-term espionage
- blackmail by so-called encryption trojans, i.e. malware that encrypts company data and promises to descript it again for a "ransom".
- interruption of all business operations
How do hackers operate?
Typical "gateways" hackers use:
- outdated software with known security vulnerabilities
- previously unknown software security gaps, so-called "zero-day exploits"
- phishing, i.e. the targeted sending of e-mails intended to trick employees into entering passwords or other sensitive data on fraudulent websites, see also our phishing awareness tool DegerPhish
- insecure passwords
- incorrect or incomplete configurations in IT systems and IT infrastructure
- e-mails with malicious attachments that install trojans, viruses, and other backdoors
- Social engineering, i.e. an attacker pretends to be a service employee and tries to gain access to sensitive data or systems in this way
- Old accounts are not deactivated and continue to be used for improper purposes

How can I protect my company against hacking and cyber crime?
DegerTech supports companies and organizations of all types and sizes with the following services:
- Pentesting
- Phishing campaigns with our phishing awareness tool DegerPhish
- Simulatedd social engineering attacks
- Extensive reports and solution concepts
- training and awareness campaigns

Our offer
One of our core services is so-called pentesting/penetration testing: In close consultation with the customer, we take on the role of a hacker and try to penetrate the IT systems in various ways and thus identify critical security gaps. In addition, we offer extensive training, awareness and consulting services. Our latest offering is our phishing simulation tool DegerPhish, which allows enterprises to run their own "phishing campaigns" in order to sensitize their employees to phishing attacks and IT security risks.
Pentesting
- Review of corporate networks, e.g. B. server infrastructure, hardened workstations, mobile devices
- Checking of network access protection
- Wifi (WLAN) checks
- Port scans and vulnerability scans
- Testing web applications in accordance with the OWASP Web Security Testing Guide and the OWASP Top 10
- API testing
- Sourcecode analysis
- Customer-specific test scenarios
Consulting
- Identification of possible weaknesses in IT systems and IT infrastructure
- Concepts and measures to eliminate existing security gaps
- Concepts for avoiding IT security issues
- Creating security awareness in your organization
IT security trainings
- Important concepts for avoiding and closing security gaps
- Security Awareness
- Typical vulnerabilities in IT systems
- Specific technologies relevant to IT security
Contact
Any questions on how your company can profit from the services of DegerTech? Contact us!
About DegerTech
DegerTech is a young IT company from the south of Germany. We have made it our task to protect companies and authorities from the increasing dangers of hacker attacks and cyber crime. The core of our services are our phishing awareness tool DegerPhish and pen testing, in which we assume the role of an attacker and as such try to discover weaknesses in our customers' IT systems and IT infrastructure. In addition, we offer training courses and other awareness measures to train your employees in IT security. For all other questions of IT security, we offer extensive advisory and consulting services.